aceofspadeshq at gee mail.com
CBD:
cbd at cutjibnewsletter.com
Buck:
buck.throckmorton at protonmail.com
joe mannix:
mannix2024 at proton.me
MisHum:
petmorons at gee mail.com
J.J. Sefton:
sefton at cutjibnewsletter.com
Public-Key Cryptography: Private Email and Secure Signatures
[Hogmartin]
Commenter Hogmartin knows a thing or two about hogs. And martins. And secure email communication (he does computer stuff for pay) which, if things go pear-shaped the way some people expect, will be quite useful in the not-so-distant future. And even if you think everything will be just wonderful, keeping private communication private is a quintessentially free man's behavior. It doesn't matter if you are swapping recipes or plans for thermonuclear devices; it isn't anyone's business but yours and the recipient.
-- CBD
You might have heard the saying, "never send anything in an email that you wouldn't send on a postcard". It's true. Email might be secure in transit - between your computer and your mail server - but it's not guaranteed. And it's even less likely that email is secure at rest: on your computer, on the recipient's computer, or even on the mail server. The document that established a common internet email system was built on earlier work that just wasn't designed for a massive public internet. If we want to be able to send and receive email that we can trust, the two main flaws that we want to address are:
- Encryption: How can I be sure that the mail I send is only readable by my intended recipient(s)?
- Signing & Validation: How can I be sure that email I receive was actually written by the person who claims to have written it?
For both of these, we can use GPG. Some of you might remember "PGP" - GPG and OpenPGP are the descendents of that and use the same workflow (and often, the same keys). The short story is that Symantec owned the rights to PGP, so the OpenPGP spec was created to establish an open standard that wasn't tied to a particular vendor, and GNU Privacy Guard is a free and open-source project that meets that standard. So, if I mention GPG or PGP or OpenPGP throughout this document, you can pretty much think of them as synonymous.
- It's free. It doesn't cost anything to install or use. There's no monthly fee, no service provider. You don't need any special hardware besides your computer.
- Once you catch on to how it works, it's pretty easy to use.
- You can use it alongside the rest of your email, in the same email account. You don't need a special address or anything.
There's one big caveat, though: you will need to install a local mail client (in this example, I'm using Mozilla Thunderbird). You can use it alongside your ordinary webmail from outlook.com or gmail.com, but you absolutely cannot send and receive encrypted messages, nor sign and verify signed messages, from the web client. If you could, you'd be handing the keys to the kingdom over to Microsoft or Google anyway. So let's not do that.
Installing and setting up Thunderbird for your mail provider is outside the scope of this tutorial. I chose it for the example because it's free, and GPG/OpenPGP functionality is built in. There's nothing else you need to download or configure, just Thunderbird. The brief summary is that you download it, install it (with the standard options - the "keep clicking next" approach), and when it starts up, it'll ask if you want to configure an existing email address. For many of the more common mail providers - gmail, Hotmail, outlook.com, verizon.net - you just tell it your email address and it'll get all the settings for you. If you're using a dedicated pseudo-anonymous address, like an 'aos.nickname@gmail' address or 'mynick@moronhorde.com', be sure not to give your real name here, just the nickname. Enter your password and you're ready to go. If you encounter any problems, you'll want to search for "configure thunderbird for verizon mail" (whatever your provider might be) to get that set up, or seek assistance from your local nerd. It might be a good idea to install Thunderbird on your preferred computer right now, and let it configure itself for your email address, just to get a feel for how it works. It should keep all the mail on the server (look for the term "IMAP" in the auto configuration screen to make sure), so you can always go back and use your webmail as usual, or switch back and forth between the web mail client and Thunderbird.
How it works
Full disclosure: this is the "hard part". It might take a while to get a handle on what's going on. Take your time. The way I'm explaining it might not be the best way for you to understand it, so feel free to ask questions in the thread or search around for other tutorials. Once the whole scheme "clicks", then you'll be able to understand it intuitively, but don't proceed until you "get it"; there's no point in generating a keypair or sending public keys around just following instructions by rote.
It might help to watch this video first, then read the steps below
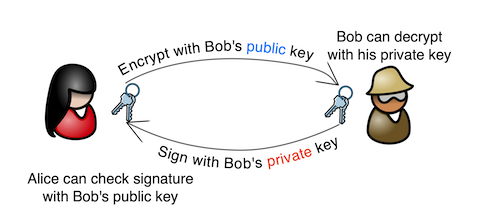
Public-key cryptography is based around the idea that with a pair of related keys (the private key and the public key), you can do some interesting one-way functions. With a public key, you can encrypt a message that can only be decrypted with the corresponding private key, and with a private key, you can sign a message that can be verified with the public key.
Between two parties (Alice and Bob):- Alice and Bob, on their own, generate their own keypair. Now Alice has her private and public key, and Bob has his private and public key.
- Alice and Bob exchange public keys. Now:
- Alice's keyring has her private key, her public key, and a copy of Bob's public key.
- Bob's keyring has his private key, his public key, and a copy of Alice's public key.
- Alice and Bob keep their private keys secret! They only exchange public keys.
- Alice wants to send a message to Bob, that only Bob can read. She types her message and encrypts it with Bob's public key, then sends the encrypted message to Bob.
- Bob receives the encrypted message from Alice. Since he has his private key, and the message was encrypted with his public key, he can decrypt and read it.
- Bob wants to reply to Alice's message. In this example, the reply doesn't need to be encryped - he doesn't care who reads it - but he wants Alice to know that he, Bob, was the one who sent the message, without any doubt.
- Bob types the reply and signs it with his private key, then sends it to Alice.
- Alice, and anyone else who gets the message, can use Bob's public key to prove that the message came from him. Only his private key could have signed the message, and anyone with his public key can validate that.
Now, they want to include Carol in the conversation. All they need is a copy of Carol's public key, and when Alice sends a message to Bob, instead of just using Bob's public key to encrypt it, she uses both Bob's and Carol's public key. The encrypted message can now be decrypted by either Bob or Carol with either of their private keys. Pretty handy! But what if Carol can get a copy of her public key to Bob, but not to Alice? That is, someone who claims to be Carol can get a copy of a public key to Alice, but Alice has no idea who it really is. Alice does trust Bob, though. Well, remember how Bob can sign a message with his private key - that only Bob has - and Alice can trust that the message really came from Bob? They can do the same thing with public keys. Bob can add a signature with his private key to Carol's public key before passing it on to Alice. Alice doesn't necessarily have to trust Carol, but she can look at Carol's public key and verify that Bob vouches for they key's authenticity by verifying his signature on Carol's public key, using her copy of Bob's public key. It might be easier to think of Carol's public key as an ordinary message: if Bob signs a message, you can be sure that it came from him. If Bob signs Carol's public key, he's vouching for its authenticity. And then it gets a bit complicated. Here's the link to the whole thing. And I will put a link to this post on the sidebar for reference. [CBD]
Comments
(Jump to bottom of comments)Posted by: AZ deplorably isolated at December 23, 2020 03:59 PM (gtatv)
Posted by: ... at December 23, 2020 04:00 PM (LCUUO)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:01 PM (L8ADy)
Posted by: Duke Lowell at December 23, 2020 04:02 PM (kTF2Z)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:02 PM (L8ADy)
Posted by: SH at December 23, 2020 04:02 PM (sX1BW)
Posted by: Inogame - Trump Won at December 23, 2020 04:02 PM (zTThE)
Posted by: ... at December 23, 2020 04:02 PM (LCUUO)
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:03 PM (dfRN6)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:01 PM (L8ADy)
I've had to use something like this before and I'm still confused by the post.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:03 PM (Zm+LZ)
Posted by: President-Elect Jane D'oh at December 23, 2020 04:03 PM (ptqGC)
Posted by: Bosk at December 23, 2020 04:03 PM (SWbVS)
Woo hoo! Who needs security? With our soon-to-come $2000 stim checks we can all rush out and buy a computer that does all that pesky thinking for us! ;-)
Sure, we'll be doomed to Weimar-style inflation and $50 bills will become toilet paper, but who cares! Show me the money baby!
Posted by: qdpsteve at December 23, 2020 04:03 PM (L2ZTs)
Posted by: wth at December 23, 2020 04:04 PM (v0R5T)
Posted by: occam's brassiere at December 23, 2020 04:04 PM (evxBY)
Posted by: JT at December 23, 2020 04:05 PM (arJlL)
This is how it's done.
¯\_(ツ)_/¯
Posted by: hogmartin at December 23, 2020 04:05 PM (t+qrx)
Posted by: Brother Tim sez: There is always More Stupid at December 23, 2020 04:05 PM (OUMaO)
Posted by: Duke Lowell at December 23, 2020 04:05 PM (kTF2Z)
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:05 PM (x8Wzq)
Posted by: The Walking Dude at December 23, 2020 04:06 PM (cCxiu)
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:06 PM (x8Wzq)
Posted by: Duke Lowell
So if he negotiates the amount left as a consideration, would that be getting down to brass tax?
Posted by: Brother Tim sez: There is always More Stupid at December 23, 2020 04:07 PM (OUMaO)
Posted by: banana Dream at December 23, 2020 04:07 PM (l6b3d)
Posted by: wth at December 23, 2020 04:07 PM (v0R5T)
Posted by: Brother Tim sez: There is always More Stupid at December 23, 2020 04:05 PM (OUMaO)
It may be possible, yes. Download and install Thunderbird, and when you configure your account, it will ask for the email address to set up. It may already have the settings. If not, ask your provider for the IMAP and SMTP settings.
Posted by: hogmartin at December 23, 2020 04:08 PM (t+qrx)
Using 2020 rules, I'm looking forward to my two weeks Christmas break turning into 9 months of vacation. All paid, of course.
Posted by: InCali at December 23, 2020 04:08 PM (9AFWN)
This is how it's done.
Posted by: hogmartin at December 23, 2020 04:05 PM (t+qrx)
If a person wants to do this, I think they should use it for everything(or at least as much as possible), not just 'important' emails. No point in flagging some emails as particularly important.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:08 PM (Zm+LZ)
Posted by: Beatgirl at December 23, 2020 04:08 PM (a1s18)
Posted by: Ward at December 23, 2020 04:08 PM (nzKWW)
Not Bob from NSA, I hope
Posted by: Hands: No Standing at December 23, 2020 04:08 PM (786Ro)
May I also recommend people looking into ProtonMail and perhaps something like ProtonVPN (or NordVPN, etc) ?
Posted by: Mordineus at December 23, 2020 04:08 PM (vx7aG)
Posted by: Berserker-Dragonheads Division at December 23, 2020 04:08 PM (9Om/r)
Posted by: wth at December 23, 2020 04:07 PM (v0R5T)
We can't see him because he's encrypted.
Posted by: TheQuietMan at December 23, 2020 04:09 PM (UnQ9z)
Posted by: brak at December 23, 2020 04:09 PM (cG+eD)
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 04:09 PM (3P/5p)
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:09 PM (x8Wzq)
Posted by: SMOD at December 23, 2020 04:09 PM (3aI0K)
Posted by: Insomniac at December 23, 2020 04:09 PM (nakwk)
Anyone know different?
Posted by: AZ deplorably isolated at December 23, 2020 04:09 PM (gtatv)
Should have posted first, Then read.
Stupid rookie mistake
Posted by: Skip at December 23, 2020 04:09 PM (Cxk7w)
Posted by: Beatgirl at December 23, 2020 04:08 PM (a1s1
---------
He's giving a talk.
Posted by: Duke Lowell at December 23, 2020 04:09 PM (kTF2Z)
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:10 PM (x8Wzq)
Posted by: Hairyback Guy at December 23, 2020 04:10 PM (R/m4+)
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:08 PM (Zm+LZ)
This is a pretty common opinion. You can set Tbird to automatically encrypt any mail (as long as you have the recipient's public key).
Posted by: hogmartin at December 23, 2020 04:10 PM (t+qrx)
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:10 PM (dfRN6)
Posted by: SMOD at December 23, 2020 04:11 PM (3aI0K)
Posted by: Beatgirl at December 23, 2020 04:11 PM (a1s18)
Posted by: Hands: No Standing at December 23, 2020 04:11 PM (786Ro)
Anyone know different?
Posted by: AZ deplorably isolated at December 23, 2020 04:09 PM (gtatv)
Even if they can(which I think is a reasonable assumption) it's no doubt a bigger strain on resources to have to decrypt everything than it is to simply record everything as the NSA does.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:11 PM (Zm+LZ)
Posted by: Beatgirl at December 23, 2020 04:11 PM (a1s1
sigh. I know.
Me no think fast.
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:11 PM (x8Wzq)
Posted by: Mordineus at December 23, 2020 04:08 PM (vx7aG)
I don't have any experience with those, but this is the thread to share if you do.
Posted by: hogmartin at December 23, 2020 04:11 PM (t+qrx)
Posted by: The Walking Dude at December 23, 2020 04:11 PM (cCxiu)
Posted by: Dr. Occupier of the President-Elect Office Without Standing Deplorable Ian Galt at December 23, 2020 04:12 PM (ufFY8)
Posted by: lowandslow at December 23, 2020 04:12 PM (qH6FZ)
I use outlook and have for ages. I'm not trusting of mozilla, especially as of late with all the crap they've started pulling on their browser. But as bad as outlook is getting, I've considered moving to SeaMonkey, which is very secure, or Evolution or Spike as well.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:12 PM (L8ADy)
Even more importantly, the fed dot gov does NOT need a warrant to examine your emails once the email hits six months old. It is considered trash/abandoned property.
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:13 PM (N3El/)
of course use Facebook and Gmail.
Big Tech is looking out for its customers
customer service is their speciality
Posted by: Johan Goldburrg at December 23, 2020 04:13 PM (r4bSV)
Posted by: Hands: No Standing at December 23, 2020 04:11 PM (786Ro)
MacOS. I spun up a Windows 8 virtual machine for the screenshots. I do run Linux, but mostly on servers and RPi.
Posted by: hogmartin at December 23, 2020 04:13 PM (t+qrx)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:13 PM (L8ADy)
Posted by: Beatgirl at December 23, 2020 04:13 PM (a1s18)
Posted by: Ben Had at December 23, 2020 04:14 PM (pxGpR)
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:10 PM (dfRN6)
.......
Sounds to me like they have some dirty little secrets.
Posted by: wth at December 23, 2020 04:14 PM (v0R5T)
Posted by: SMOD at December 23, 2020 04:14 PM (3aI0K)
Posted by: Bob, NSA at December 23, 2020 04:14 PM (gmo/4)
Anyone know different?
Posted by: AZ deplorably isolated at December 23, 2020 04:09 PM (gtatv)
It's still dependent on the length of your hash and at some point them just busting down your door to wave a rifle in your face is much easier. It's always about reaching a balance between the value of the information and the energy/time (power) required to break its obfuscation.
Posted by: banana Dream at December 23, 2020 04:14 PM (l6b3d)
what is the name of the email service that shut down the Norther Virginia Tea Party email because they wanted to block a Trump PRalley in DC?
Posted by: will choose a nic later at December 23, 2020 04:14 PM (r4bSV)
Joe Biden
Source : https://bit.ly/38qY4tG
Posted by: Neutral Observer at December 23, 2020 04:14 PM (abHAZ)
Posted by: AltonJackson at December 23, 2020 04:14 PM (ymQXP)
Posted by: Duke Lowell at December 23, 2020 04:14 PM (kTF2Z)
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:10 PM
SO Carol and Ted are hooking up elsewhere?
Posted by: Skip at December 23, 2020 04:14 PM (Cxk7w)
Anyone know different?
Posted by: AZ deplorably isolated at December 23, 2020 04:09 PM (gtatv)
For sensitive communications, it's always useful to use a cypher as well. Word substitution, one example use chess terminology. For discussing a limited number of persons, assign them a chess designation, frex white queen, kings bishop black. The code talkers in WW2 would use animal names.
Posted by: Tom Servo at December 23, 2020 04:14 PM (trdmm)
Posted by: InCali at December 23, 2020 04:14 PM (9AFWN)
Posted by: Martini Farmer at December 23, 2020 04:15 PM (3H9h1)
Posted by: JROD at December 23, 2020 04:15 PM (0jZnq)
Posted by: Skip at December 23, 2020 04:14 PM (Cxk7w)
I prefer Stacy's Mom.
Posted by: President-Elect anchorbabe fashion cop at December 23, 2020 04:15 PM (ufFY8)
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 04:09 PM (3P/5p)
Only that I've heard that quantum computers are really good at the sort of math that PGP/GPG relies on.
Posted by: hogmartin at December 23, 2020 04:15 PM (t+qrx)
Posted by: Archer at December 23, 2020 04:16 PM (gmo/4)
For sensitive communications, it's always useful to use a cypher as well. Word substitution, one example use chess terminology. For discussing a limited number of persons, assign them a chess designation, frex white queen, kings bishop black. The code talkers in WW2 would use animal names.
Posted by: Tom Servo
Statsi, politburo, history gives us many useful terms for even casual use. Steiner.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:16 PM (Zm+LZ)
Posted by: Ward at December 23, 2020 04:16 PM (nzKWW)
Posted by: Duke Lowell at December 23, 2020 04:16 PM (kTF2Z)
I'm not sure I could successfully install a private, secure email account, but the day is coming when it will be absolutely necessary.
Posted by: Ladyl at December 23, 2020 04:16 PM (TdMsT)
Posted by: wth at December 23, 2020 04:07 PM (v0R5T)
==========
Bob is hung like mule, he can handle Alice and Carol and has no use for Ted.
Lucky Bastard
Posted by: Bonecrusher at December 23, 2020 04:16 PM (JNTt1)
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:13 PM (N3El/)
The problem we all have is while this is cool if you're all on the same page so to speak, it doesn't help when all of your friends use gmail or yahoo. Just like they always click "okay" when installing an app on their android that wants to access contacts, camera, photos, video, mic, etc. So goolag has your photos and contact info.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:16 PM (L8ADy)
Posted by: Dr. Occupier of the President-Elect Office Without Standing Deplorable Ian Galt at December 23, 2020 04:16 PM (ufFY8)
This can be accomplished relatively inexpensively.
Posted by: Thomas Bender at December 23, 2020 04:17 PM (qv4OB)
Got into wan and lan communications soon after.
Posted by: AZ deplorably isolated at December 23, 2020 04:17 PM (gtatv)
Posted by: Archer at December 23, 2020 04:17 PM (gmo/4)
Posted by: Archer at December 23, 2020 04:17 PM (gmo/4)
-----------
How?
Posted by: Duke Lowell at December 23, 2020 04:17 PM (kTF2Z)
Posted by: Alice at December 23, 2020 04:18 PM (v0R5T)
ham radio license or use carrier pigeons and zodiac code. If things go
south you can always have roast pigeon
I use thunderbird on Linux for this stuff. Took me all of about 2 minutes to set it up. Just went into "Add Ons" and searched for "pgp". Couple of clicks later and I had a suitable extension installed and working.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:18 PM (SchxB)
Posted by: AZ deplorably isolated at December 23, 2020 04:09 PM (gtatv)
If they they are after you that bad they will bust down your door with a warrant.
A one time cipher pad would also be useful for really sensitive comms.
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:18 PM (N3El/)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:16 PM (L8ADy)
*dingding*
And all encrypted correspondence is only as secure as the least secure private key in the chain.
Posted by: hogmartin at December 23, 2020 04:18 PM (t+qrx)
Posted by: Tom Servo
Statsi, politburo, history gives us many useful terms for even casual use. Steiner.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:16 PM (Zm+LZ)
Back when we gave a shit, everything was done over a Cisco VPN as well.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:18 PM (L8ADy)
Posted by: Ladyl at December 23, 2020 04:16 PM (TdMsT)
You can run this with your regular email address, alongside your ordinary mail.
Posted by: hogmartin at December 23, 2020 04:19 PM (t+qrx)
Posted by: Bertram Cabot, Jr. at December 23, 2020 04:19 PM (63Dwl)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:16 PM (L8ADy)
*dingding*
And all encrypted correspondence is only as secure as the least secure private key in the chain.
Posted by: hogmartin at December 23, 2020 04:18 PM (t+qrx)
Assuming chains of communications are compromised leads to useful thought exercises. Like how are they monitoring and analyzing these communications, how tight is the net really in effect? Just because everything is recorded doesn't mean everything is read.
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:19 PM (Zm+LZ)
Q: Isn't my ISP logging every key stroke I make?
Posted by: Brave Sir Robin at December 23, 2020 04:20 PM (LuIJt)
Posted by: Ward at December 23, 2020 04:20 PM (nzKWW)
I haven't looked at it in a while.
Just checked now, and he is still around.
Posted by: Dr. Occupier of the President-Elect Office Without Standing Deplorable Ian Galt at December 23, 2020 04:20 PM (ufFY8)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:16 PM (L8ADy)
Very true, so you have to train the people you communicate with the concept of OPSEC. If they don't grok the concept they don't get sensitive comms.
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:20 PM (N3El/)
I get commercials in Navajo off the Flagstaff radio station. Seems to mostly be about Covid.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:20 PM (SchxB)
Posted by: Mark1971 at December 23, 2020 04:20 PM (xPl2J)
Posted by: Robert at December 23, 2020 04:20 PM (tdndJ)
Jan. 17th, 2021: The LARGEST Armed Protest Ever To Take Place On American Soil Is Scheduled
Peaceful Armed Demonstrations Are Scheduled On January 17th, 2021 at Noon Local Time At Each US Capital City and Washington DC.
... this should be interesting
Posted by: SMOD at December 23, 2020 04:21 PM (3aI0K)
Posted by: TheQuietMan at December 23, 2020 04:21 PM (UnQ9z)
I'm the guy that complains about those barcoded resturaunt menus.... I make them bring me a real menu.
Posted by: Ward
Is that something you need a smartphone to use?
Posted by: Bertram Cabot, Jr. at December 23, 2020 04:21 PM (63Dwl)
Posted by: brak at December 23, 2020 04:09 PM (cG+eD)
That's true, though it's also true for recipients when you're using GPG. The recipient has to set up their end, or you're just using regular email.
The problem with third party encrypted apps is you're trusting them to do their own security directly. Not only that they prevent intrusions, but also that they tell you if an intrusion occurred. How likely is it really they'd tell you if they got hacked?
Posted by: Ace's liver at December 23, 2020 04:22 PM (wGeit)
If I'm reading between the lines right, Bob and Alice got it goin' on.
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:10 PM (dfRN6)
If Ralph finds out Bang! Zoom! Right to the moon for Alice.
Posted by: TheQuietMan at December 23, 2020 04:22 PM (UnQ9z)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:22 PM (VNmG1)
Posted by: Warlord Someguy - General Who Pacifies The East and West at December 23, 2020 04:19 PM (Zm+LZ)
They use keywords and batch like things. Most stuff will never get seen if there are no hot buzzwords used.
Unless they have reason to look at you. Then all bets are off.
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:22 PM (N3El/)
Posted by: Archer at December 23, 2020 04:22 PM (gmo/4)
Posted by: Skip at December 23, 2020 04:22 PM (Cxk7w)
Posted by: bonhomme at December 23, 2020 04:23 PM (i0wNm)
communicate with the concept of OPSEC. If they don't grok the concept
they don't get sensitive comms.
Posted by: AZ Hi Desert (Gringo fuertemente armado-Si Vis Pacem, Pac Bellum) at December 23, 2020 04:20 PM (N3El/)
Don't believe in any notion of privacy or anonymity on the Internet. If you want it to stay secret - don't type it on a keyboard.
I'm not commenting on what should be "right" - a man's papers and effects should be confidential in the mail, which would imply the same over the Internet. But that's not how it works. Because our digital postmen not only open everything - they offer new and shiny services all the time to get us to let them handle our mail.
Posted by: Endeavor To Persevere at December 23, 2020 04:24 PM (Op9So)
Posted by: TheQuietMan at December 23, 2020 04:22 PM (UnQ9z)
------
WHEN he finds out.
They think they're all secure and everything with their fancy-shmancy keys and stuff, but it'll come out. It always comes out.
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:24 PM (dfRN6)
It's probably not as hard as people think. A moment ago, I just logged into my webmail account. I clicked on Options, and it had a link to instructions on how to make my webmail work with Thunderbird (among other email programs.)
Don't be intimidated.
Posted by: Hands at December 23, 2020 04:24 PM (786Ro)
.......
Joe should show up and talk about darkest days ahead and how we are doomed.
Posted by: wth at December 23, 2020 04:24 PM (v0R5T)
lol j/k. I am going to send this to my husband and what I can't figure out he can probably help me. Just takes some time. Thanks for sharing this hogmartin.
Posted by: Jewells45TRUMPWON! at December 23, 2020 04:24 PM (nxdel)
I'm the guy that complains about those barcoded resturaunt menus.... I make them bring me a real menu.
Posted by: Ward
Is that something you need a smartphone to use?
-----------------
Yep. If printing menus makes that much difference in their business model they are doing it wrong.
Posted by: Ward at December 23, 2020 04:24 PM (nzKWW)
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:24 PM (GbPPJ)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:16 PM (L8ADy)
======
Bothers me to end that I pay a monthly fee for Pandora, but then every third they song they play, just by coincidence I'm sure, is a song I happen to already have in my phones library.
Posted by: 6-4-3 at December 23, 2020 04:24 PM (1aJ+m)
Posted by: Archer at December 23, 2020 04:24 PM (gmo/4)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:24 PM (SchxB)
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:24 PM (dfRN6)
This is about me, isn't it?
Posted by: Anthony Weiner at December 23, 2020 04:25 PM (tdndJ)
What hogmartin is talking about, Thunderbird, is an application you install on your computer so you can access your email without having to go to some big tech website like gmail or hotmail).
Posted by: Hands at December 23, 2020 04:25 PM (786Ro)
Example: Xer furry, victm 'f indgus pepol uptwinkle unconcus bias.
Translation: At dawn meet behind the food depot for an arms delivery.
Posted by: banana Dream at December 23, 2020 04:25 PM (l6b3d)
=====
To NO end
Posted by: 6-4-3 at December 23, 2020 04:25 PM (1aJ+m)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:22 PM (VNmG1)
I've used every metaphor for PKE that there is in presentations, and have never found one that everyone gets intuitively. But once it clicks, then it's obvious.
Posted by: hogmartin at December 23, 2020 04:25 PM (t+qrx)
=============
"Mississippi Queen" is a masterpiece. You know what's great about it? It knows when to stop.
Posted by: Brave Sir Robin at December 23, 2020 04:26 PM (LuIJt)
Q: Isn't my ISP logging every key stroke I make?
Posted by: Brave Sir Robin at December 23, 2020 04:20 PM (LuIJt)
Supposedly, goolag's AI is so advanced it can recognize a user simply by their keystrokes. Wive's tale or not, you know they're working on it.
I have no doubt while not every email is read, they're certainly stored. If at any point a keyword becomes "hot" they'll refer to the archives, and of course read everything going forward. So yeah, we'll need to use code and nondescript keywords/phrases for what/when to change.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:26 PM (L8ADy)
Posted by: Old Blue
BTDT!
HR at the job referenced above asked me how I got recognition for my work. I told them that if no one knew the encryption was there and working I had succeeded. The 2 HR women did *NOT* get it.
Posted by: AZ deplorably isolated at December 23, 2020 04:26 PM (gtatv)
Posted by: Ward at December 23, 2020 04:24 PM (nzKWW)
Right now, it's about the COVID restrictions. Every single penny that can be saved helps.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:26 PM (GbPPJ)
Posted by: Archer at December 23, 2020 04:27 PM (gmo/4)
Posted by: SMOD at December 23, 2020 04:21 PM (3aI0K)
I wonder how many of Obama's army will be there?
Posted by: CN at December 23, 2020 04:27 PM (ONvIw)
Posted by: Hands at December 23, 2020 04:25 PM (786Ro)
Right. Any time you're using your browser to type up a message, it is by its nature, not end-to-end encrypted. Otherwise, you'd have a copy of your private key on Google's server. Which would be a terrible idea.
Posted by: hogmartin at December 23, 2020 04:27 PM (t+qrx)
Posted by: Blanco Basura - moronhorde.com lives again
Diabetes is COVID co-morbidity big time, unfortunately ...
Posted by: Adriane the I Wish This was a Movie, So I Could Walk Out Critic ... at December 23, 2020 04:27 PM (LPnfS)
Posted by: Duke Lowell at December 23, 2020 04:27 PM (kTF2Z)
Posted by: Ben Had at December 23, 2020 04:28 PM (pxGpR)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:28 PM (VNmG1)
Posted by: sniffybigtoe at December 23, 2020 04:28 PM (Ti1eN)
Posted by: CN at December 23, 2020 04:29 PM (ONvIw)
Posted by: Sgt. Stedenko at December 23, 2020 04:29 PM (ntg4m)
Posted by: CN at December 23, 2020 04:29 PM (ONvIw)
Posted by: hogmartin at December 23, 2020 04:25 PM (t+qrx)
The hard part for me has always been accepting you can't generate the public key from the private key or vice versa, but you can encrypt something with one key and decrypt it with the other. That's all math black magic that seems to violate the laws of goodness and rightness.
Posted by: Ace's liver at December 23, 2020 04:29 PM (wGeit)
Supposedly that's what all those random standing in the woods looking at trees pictures that Comey puts up really are.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:29 PM (GbPPJ)
Posted by: dartist at December 23, 2020 04:29 PM (+ya+t)
Posted by: sniffybigtoe at December 23, 2020 04:28 PM (Ti1eN)
Balls of steel.
Scrotum of leather.
Pubes of razor wire.
Posted by: Anthony Weiner at December 23, 2020 04:29 PM (tdndJ)
Now I'm going to have to go find out if some smart ass coder put together a mail client and called it Ripple.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:29 PM (SchxB)
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:24 PM (GbPPJ)
Also check SeaMonkey.
Not commie owned, and open source based on the original Mozilla code. Mac OS, Windows and Linux.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:30 PM (L8ADy)
Posted by: Mitch Probably at December 23, 2020 04:30 PM (f5M0A)
The #COVID19 package, while imperfect, will save jobs and lives. The sooner the bill becomes law - the better.
It will allow millions of businesses to avoid bankruptcy, deliver vaccines even faster, help those unemployed and provide money for families who are struggling.
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 04:30 PM (3P/5p)
Posted by: Mishdog at December 23, 2020 04:31 PM (F/Rk0)
Not commie owned, and open source based on the original Mozilla code. Mac OS, Windows and Linux.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:30 PM (L8ADy)
Do you know if their mail client has a GPG plug-in?
Posted by: hogmartin at December 23, 2020 04:31 PM (t+qrx)
many thanks !
COMSEC / OPSEC is the best Christmas gift for 2020 !
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 04:31 PM (pmEbq)
but no one has them
Posted by: Skip at December 23, 2020 04:31 PM (Cxk7w)
Posted by: Gilded at December 23, 2020 04:31 PM (BRkq2)
$699
https://bit.ly/2Jm8VwA
Posted by: b
you have to be mystified by any guy that hates himself enough to buy hk guns.
Posted by: confederatefifth at December 23, 2020 04:31 PM (4Jold)
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:31 PM (L8ADy)
Posted by: Insomniac at December 23, 2020 04:32 PM (nakwk)
Posted by: Georgia Secretary of State at December 23, 2020 04:32 PM (8DRUP)
Posted by: confederatefifth at December 23, 2020 04:32 PM (4Jold)
Posted by: iandeal at December 23, 2020 04:32 PM (vgGyZ)
Posted by: hogmartin at December 23, 2020 04:32 PM (t+qrx)
Posted by: dartist at December 23, 2020 04:32 PM (+ya+t)
I don't understand how my computer knows how to encrypt something using only Bob's public key, in a way only he can unencrypt it (only with his private key). If my computer can so encrypt it, why can't my computer know how to unencrypt it (and so why can't anyone else also do that, anyone that has Bob's public key)?
There is probably some coding trick involved? Or I am missing a point or two.
Posted by: illiniwek at December 23, 2020 04:32 PM (Cus5s)
The #COVID19 package, while imperfect, will save jobs and lives. The sooner the bill becomes law - the better.
----------------------
Imperfect...spit!
Posted by: Ward at December 23, 2020 04:33 PM (nzKWW)
Q: Isn't my ISP logging every key stroke I make?
Posted by: Brave Sir Robin at December 23, 2020 04:20 PM (LuIJt)
They are logging all DNS requests so no keystroke logging but EVERY site you visit, yes.
Posted by: WinLinBSDAdmin at December 23, 2020 04:33 PM (KXkkH)
Posted by: Insomniac at December 23, 2020 04:32 PM (nakwk)
---------
Twenty bucks, you know the rest.
Posted by: Duke Lowell at December 23, 2020 04:33 PM (kTF2Z)
Posted by: hogmartin at December 23, 2020 04:33 PM (t+qrx)
I do not understand at all, not in the slightest, the whole embed messages in pictures thing.
Supposedly that's what all those random standing in the woods looking at trees pictures that Comey puts up really are.
Steganography is just obscuring what you're sending. Like shipping a dozen needles using haystacks as carriers.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:33 PM (SchxB)
I 1000% prefer the menu on my phone. I don't have to worry about what psychopath has been touching the menu and what was on their hands.
Posted by: bonhomme at December 23, 2020 04:33 PM (i0wNm)
Posted by: Insomniac at December 23, 2020 04:32 PM (nakwk)
Price of...?
Posted by: hogmartin at December 23, 2020 04:33 PM (t+qrx)
Oh, derp. Never mind.
Posted by: hogmartin at December 23, 2020 04:33 PM (t+qrx)
Posted by: CN at December 23, 2020 04:33 PM (ONvIw)
Posted by: Bosk at December 23, 2020 04:34 PM (SWbVS)
Posted by: hogmartin at December 23, 2020 04:31 PM (t+qrx)
Yes, if it works with Thunderbird it usually works with SeaMonkey.
Check PortableApps
https://portableapps.com/node/43675
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:34 PM (L8ADy)
The #COVID19 package, while imperfect, will save jobs and lives. The sooner the bill becomes law - the better.
......
What's his cut?
Posted by: wth at December 23, 2020 04:34 PM (v0R5T)
Supposedly that's what all those random standing in the woods looking at trees pictures that Comey puts up really are.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:29 PM (GbPPJ)
-------------------
The message is rather simple: Comey is letting the world know that he is a sanctimonious twit. Well, that's the message conveyed, not what is intended.
Posted by: blake - Dr semi lurker in marginal standing at December 23, 2020 04:34 PM (WEBkv)
Posted by: Brother Tim sez: There is always More Stupid at December 23, 2020 04:35 PM (OUMaO)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:33 PM (SchxB)
Thank you, I couldn't even remember what it was called.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:35 PM (GbPPJ)
Posted by: wth at December 23, 2020 04:07 PM
Ted's dead, wth....Ted's dead.
*starts chopper*
Posted by: Butch at December 23, 2020 04:35 PM (ejd/p)
Posted by: confederatefifth at December 23, 2020 04:32 PM (4Jold)
Oh man, some of those old Cheney jokes here were something.
Posted by: clutch cargo now with 21% more FUCKITOL at December 23, 2020 04:35 PM (L8ADy)
Posted by: johnd01 at December 23, 2020 04:36 PM (TXvM3)
Q: Isn't my ISP logging every key stroke I make?
Posted by: Brave Sir Robin at December 23, 2020 04:20 PM (LuIJt)
FYI-I use encrypted DNS (DNSCrypt) for my personal systems.
Posted by: WinLinBSDAdmin at December 23, 2020 04:36 PM (KXkkH)
You don't have to, that's what we're here for.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:36 PM (SchxB)
Posted by: confederatefifth at December 23, 2020 04:36 PM (4Jold)
Posted by: davidt at December 23, 2020 04:36 PM (l3+k2)
Posted by: Mr Aspirin Factory at December 23, 2020 04:36 PM (89T5c)
I have a HK P2000 in .40. It's my favorite carry gun.
I don't think I hate myself.
Posted by: bonhomme at December 23, 2020 04:36 PM (i0wNm)
Or is it the other way around?
Posted by: Minuteman at December 23, 2020 04:36 PM (JFvl/)
The #COVID19 package, while imperfect, will save jobs and lives. The sooner the bill becomes law - the better.
Thanks Lindsey. There are less than 400 million Americans according to the last census. If we gave every one of them $600 bucks - the math works like this.
Six times four equals twenty four. Now add four zeroes. That's $240,000 million dollars. Now take away three zeroes, because a billion is just 1,000 million. Well - we're just talking about $240 billion. A tad shy of the $900 billion that latest GOPe reach around the aisle is going to cost. Thanks Lindsey.
Posted by: Endeavor To Persevere at December 23, 2020 04:36 PM (Op9So)
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:36 PM (+y/Ru)
Posted by: illiniwek at December 23, 2020 04:32 PM (Cus5s)
I actually don't know the math behind it. But it's the math. If it helps to think of a public key as a secure lockbox that only the private key can unlock, and the act of encrypting with the public key is putting a message in the lockbox (and now you can't retrieve it again), it's kinda like that.
Posted by: hogmartin at December 23, 2020 04:36 PM (t+qrx)
Posted by: wth at December 23, 2020 04:07 PM
Ted's dead, wth....Ted's dead.
*starts chopper*
Posted by: Butch at December 23, 2020 04:35 PM (ejd/p)
--------
"Aw, Ted...Don't be dead, dude!"
- Bill S. Preston, Esq.
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:37 PM (dfRN6)
It's a one-way algorithm - once you go from point a to point b, i.e. once you encrypt a set of bits, you can't get back to point a with the same key. If you could then it would be "symmetric" encryption, and not very useful for this application.
Posted by: Ace's liver at December 23, 2020 04:37 PM (wGeit)
The #COVID19 package, while imperfect, will save jobs and lives.
Whose? Venezuelan's - Nepalese? This is pretty poor political trade craft here...it's over the top drama queen stuff that isn't going to counter anything Trump says...
Posted by: Boswell at December 23, 2020 04:37 PM (w2LAm)
Posted by: Brad at December 23, 2020 04:37 PM (FTIES)
They tried hiding things in the real dinosaurs, but it proved hard to find a working one.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:37 PM (SchxB)
I don't think I hate myself.
Posted by:
was a tease, friends have many of them, the thing is is, they believe that they manufacture great guns, but hate their retail clients.
Posted by: confederatefifth at December 23, 2020 04:38 PM (4Jold)
Posted by: johnd01
Yeah, but you have to stick it through the barrier to get to the magic dot.
Posted by: Brother Tim sez: There is always More Stupid at December 23, 2020 04:38 PM (OUMaO)
The #COVID19 package, while imperfect, will save jobs and lives. The sooner the bill becomes law - the better.
And Peruvian trannies will be better for it.
Posted by: That guy who always says... at December 23, 2020 04:38 PM (W4eKo)
They tried hiding things in the real dinosaurs, but it proved hard to find a working one.
Posted by:
the hiding in the dinosaur is easy, the getting it back out is the hard thing.
Posted by: confederatefifth at December 23, 2020 04:38 PM (4Jold)
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:38 PM (+y/Ru)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:36 PM (SchxB)
Distributed Horde knowledge is amazing. And terrifying.
I was re reading Lucifer's Hammer the other day and though the Horde could get everything back up and running in no time, considering all the Horde knows.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:39 PM (GbPPJ)
Posted by: WinLinBSDAdmin at December 23, 2020 04:39 PM (KXkkH)
Should just need a skeleton key at this point.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:39 PM (SchxB)
Posted by: Mr Aspirin Factory at December 23, 2020 04:36 PM (89T5c)
Lindsey, stop looking at me while I do you!
Posted by: Zombie John McCain at December 23, 2020 04:39 PM (L8ADy)
Posted by: President-Elect anchorbabe fashion cop at December 23, 2020 04:40 PM (ufFY8)
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:38 PM (+y/Ru)
I pfftt don't pfftt understand pfftt a pfftt thing pfftt you're pfftt saying.
Posted by: DR.WTF at December 23, 2020 04:40 PM (AiZBA)
Posted by: confederatefifth at December 23, 2020 04:40 PM (4Jold)
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 04:41 PM (pmEbq)
It is just so easy to copy and store anything digital. Printers all create hidden dots on every document to identify the source. It use to be yellow dots visible with a blue light. Now I cannot even find these. They are still there. The printer is identified on every counterfeit currency made with digital equipment.
I trust nothing electronic. I don't trust the US mail but, something written in long hand sent by regular mail from a USPO blue box is going to have protection if you trust the recipient and the deep state is not aware of them. A note written in long hand and burned by the recipient is about the best you can do short of carrier pigeon. Still best to use code words like "delicious pizza" IYKWIMAITYD.
Posted by: FlimFlamed at December 23, 2020 04:41 PM (ZTDnL)
Posted by: Mr Aspirin Factory at December 23, 2020 04:36 PM (89T5c)
The election is over. It's time for that sudden but inevitable betrayal.
Posted by: Ace's liver at December 23, 2020 04:42 PM (wGeit)
Posted by: confederatefifth at December 23, 2020 04:42 PM (4Jold)
Posted by: Insomniac at December 23, 2020 04:42 PM (nakwk)
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 04:42 PM (3P/5p)
Posted by: Archer at December 23, 2020 04:24 PM (gmo/4)
From my experience? They say either the dude sitting behind them is an accomplished percussionist time keeper with the accuracy of an atomic clock, or they say the baboon sitting behind them is just a beater and might as well be beating on garbage cans with a hammer.
Posted by: Berserker-Dragonheads Division at December 23, 2020 04:43 PM (9Om/r)
Posted by: Ben Had at December 23, 2020 04:43 PM (pxGpR)
Posted by: hogmartin at December 23, 2020 04:33 PM (t+qrx)
Oh, derp. Never mind.
Posted by: hogmartin
I admit I snickered.
Posted by: AZ deplorably isolated at December 23, 2020 04:43 PM (gtatv)
Posted by: Berserker-Dragonheads Division at December 23, 2020 04:43 PM (9Om/r)
--------------
And when the drums stop, the bass solo starts!
Posted by: blake - Dr semi lurker in marginal standing at December 23, 2020 04:43 PM (WEBkv)
Posted by: Beatgirl at December 23, 2020 04:44 PM (a1s18)
Posted by: No One of Consequence at December 23, 2020 04:44 PM (CAJOC)
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:38 PM (+y/Ru)
.......
Ah. Esperanto.
Posted by: wth at December 23, 2020 04:44 PM (v0R5T)
You never know when.you might need CPR.
https://youtu.be/hyMMw_WRi_I
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:44 PM (+y/Ru)
I know, I was teasing back.
> friends have many of them, the thing is is, they believe that they manufacture great guns, but hate their retail clients.
Yeah, it was a bit pricey. I've also heard HK can suck to deal with if you need them to do a repair. HK also doesn't listen to what potential customers want, they'll tell YOU what you want.
Posted by: bonhomme at December 23, 2020 04:44 PM (i0wNm)
Old Firm had a defendant find that out the hard way when we got some discovery in and I was going through the printed out emails and noticed there was a whole set that didn't match up with the electronic files.
We got paid off A LOT, I mean the company decided to reevaluate the settlement offer, before having to provide those emails.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:44 PM (GbPPJ)
Posted by: Berserker-Dragonheads Division at December 23, 2020 04:43 PM (9Om/r)
. . . and then there is Dave Lombardo.
Posted by: Pug Mahon, Confuzzled at December 23, 2020 04:44 PM (x8Wzq)
Posted by: Archer at December 23, 2020 04:24 PM (gmo/4)
RING DING DING DING DING A DING A DING!!
Oh wait, that's the fox. Never mind.
Posted by: Insomniac at December 23, 2020 04:45 PM (nakwk)
open source and are based in Switzerland with decent privacy standards.
Moronhorde.com also uses open source, but that's because I'm a cheap bastard. It's also why it's hosted on a low cost hosting provider.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:45 PM (SchxB)
Posted by: confederatefifth at December 23, 2020 04:46 PM (4Jold)
https://youtu.be/hyMMw_WRi_I
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:44 PM (+y/Ru)
=======
Heh. I did some cardio with my daughter at the gym last night. I told her to find out where the AED is first.
Posted by: 6-4-3 at December 23, 2020 04:46 PM (1aJ+m)
So you've watched my show!
You're a Great American!
Posted by: Sean Hannity at December 23, 2020 04:46 PM (3P/5p)
Posted by: Mitch Probably at December 23, 2020 04:30 PM (f5M0A)
Corrected, thank you (and CBD)
Posted by: hogmartin at December 23, 2020 04:47 PM (t+qrx)
Posted by: sniffybigtoe at December 23, 2020 04:28 PM (Ti1eN)
Great.
Who is going to protect our Nation's borders now?
Posted by: Burnt Toast at December 23, 2020 04:47 PM (/Dgcm)
once you encrypt a set of bits, you can't get back to point a with the
same key."
I can accept they can do it ... and that "it's the math" ... still doesn't make sense to me. Any math operations my computer does should be undoable ... just reverse the math.
Obviously this is more alien technology ... the good aliens. I'll accept it on faith, along with relativity and dark matter.
Posted by: illiniwek at December 23, 2020 04:47 PM (Cus5s)
Posted by: Weasel at December 23, 2020 04:47 PM (MVjcR)
Rule for work:
Don't put anything into any work related channel that you don't want to hear read out in court.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:48 PM (SchxB)
Posted by: Weasel at December 23, 2020 04:47 PM (MVjcR)
Just send it in Authentic Frontier Gibberish. Only a select few will be able to interpret it.
Posted by: Insomniac at December 23, 2020 04:48 PM (nakwk)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:48 PM (SchxB)
----------------
Or forwarded.
Posted by: blake - Dr semi lurker in marginal standing at December 23, 2020 04:49 PM (WEBkv)
Posted by: Weasel at December 23, 2020 04:47 PM (MVjcR)
Just send it in Authentic Frontier Gibberish. Only a select few will be able to interpret it.
Posted by: Insomniac at December 23, 2020 04:48 PM (nakwk)
--------
What the hell happened to decoder rings, anyhow?
Posted by: Weasel at December 23, 2020 04:49 PM (MVjcR)
Posted by: Old Doc Beartooth at December 23, 2020 04:50 PM (vgGvZ)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:50 PM (VNmG1)
Even the Jihadis went back to electronic communications eventually. There's just too much of an efficiency hit to send all your messages by trusted courier or some such.
Posted by: Ace's liver at December 23, 2020 04:50 PM (wGeit)
Pop is how we used to setup email. It saves a copy of the message to your computer or device. It only looks at the inbox, trash and sent items. It can't really be synced across multiple devices.
Imap is like looking at the mail server or webmail. It will sync with any custom folders there but leaves the messages out on the mail server. Easier to see the same messages across multiple devices this way.
Posted by: Notsothoreau - look forward at December 23, 2020 04:50 PM (YynYJ)
It's a bit of a pain but that's the tradeoff: security vs convenience.
Posted by: Mark Andrew Edwards, shotguns solve problems at December 23, 2020 04:51 PM (d1uFV)
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 04:51 PM (+y/Ru)
Don't put anything into any work related channel that you don't want to hear read out in court.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:48 PM (SchxB)
By your worst enemy in the nastiest tone possible.
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:51 PM (GbPPJ)
Posted by: confederatefifth at December 23, 2020 04:31 PM (4Jold)
Blow me.
I had two (before the accident), a USP .40 and a VP9, and they are both rock-solid reliable and pretty accurate (the 9mm is better than the .40).
Posted by: CharlieBrown'sDildo at December 23, 2020 04:51 PM (xT2tT)
Posted by: confederatefifth at December 23, 2020 04:52 PM (4Jold)
Posted by: illiniwek at December 23, 2020 04:47 PM (Cus5s)
From my (limited) understanding, it's completely possible to reverse the operation and decrypt the message, but computationally unfeasible in a human lifetime for a 4096-bit key. Search for "how long to break 4096 bit rsa" for more on that.
Posted by: hogmartin at December 23, 2020 04:52 PM (t+qrx)
Posted by: Ray Charles at December 23, 2020 04:52 PM (sjdRT)
Posted by: Archer at December 23, 2020 04:24 PM (gmo/4)
RING DING DING DING DING A DING A DING!!
Oh wait, that's the fox. Never mind.
Posted by: Insomniac at December 23, 2020 04:45 PM (nakwk)
LOL
Posted by: Mark Andrew Edwards, shotguns solve problems at December 23, 2020 04:52 PM (d1uFV)
Except the ones that cranked out counterfeit ballots.
Posted by: Burnt Toast at December 23, 2020 04:52 PM (/Dgcm)
Posted by: Jewells45TRUMPWON! at December 23, 2020 04:52 PM (nxdel)
Posted by: illiniwek at December 23, 2020 04:47 PM (Cus5s)
Yeah, as I wrote earlier my whole discomfort with asymmetric encryption is I have to trust the eggheads involved because my math skills aren't up to the task of verification.
Posted by: Ace's liver at December 23, 2020 04:52 PM (wGeit)
Posted by: Hillary at December 23, 2020 04:53 PM (l3+k2)
I had two (before the accident), a USP .40 and a VP9, and they are both rock-solid reliable and pretty accurate (the 9mm is better than the .40).
Posted by: CharlieBr
it gets more interesting the further you get into the thread.
by the way, didn't you get rid of the hks?
Posted by: confederatefifth at December 23, 2020 04:53 PM (4Jold)
Posted by: sniffybigtoe at December 23, 2020 04:28 PM (Ti1eN)
Great. Who is going to protect our Nation's borders now?Posted by: Burnt Toast at December 23, 2020 04:47 PM (/Dgcm)
Spoiler Alert - Nobody in FedGov will protect the borders. Regardless of how much money you throw at them. It's like trying to find true love at a strip club. It's just not gonna' happen - no matter how much you want it to.
But they'll sell you on the illusion as long as you keep making it rain.
Posted by: Endeavor To Persevere at December 23, 2020 04:53 PM (Op9So)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:54 PM (VNmG1)
Posted by: Old Blue - Deplorable Trump Chump at December 23, 2020 04:50 PM (VNmG1)
And something with a 129 bit key (if i understand right) would be twice as hard to break, for that algorithm.
Posted by: hogmartin at December 23, 2020 04:55 PM (t+qrx)
I'll probably regret that offer pretty soon.
Why send an email? Because I'm not sending your initial password back in the comments here, and I don't have everyone's phone numbers to text it to you.
And if you put your phone number here I'm not responsible for the flood of texts and phone calls you'll be getting.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:55 PM (SchxB)
Posted by: Old Blue - D
wait, they are coming out with the 4097s in jan.
Posted by: confederatefifth at December 23, 2020 04:55 PM (4Jold)
Vote harder.
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 04:55 PM (3P/5p)
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:44 PM (GbPPJ)
This is the problem is with defamation law suits...you're emails, I mean you, the plaintiff, other than to your attorneys, are discoverable. And they are typically damning, as you discuss nebulous and potentially self-defeating ways to get around and sue people for things you don't want them saying.
Posted by: Boswell at December 23, 2020 04:55 PM (w2LAm)
Posted by: Jewells45TRUMPWON! at December 23, 2020 04:52 PM (nxdel)
Woo! QT cafe or ONT then, or email. AltonJackson sounded interested too.
Posted by: hogmartin at December 23, 2020 04:56 PM (t+qrx)
Posted by: BifBewalski AOS Moron at December 23, 2020 04:56 PM (VcFUs)
Is this gonna be on the final?
Posted by: Zombie Robbo the Llama Butcher at December 23, 2020 04:03 PM (dfRN6)
Yep... like keeping your powder dry/how to:-P
Posted by: redbanzai the Southerner at December 23, 2020 04:56 PM (946rW)
Posted by: SMOD at December 23, 2020 04:57 PM (3aI0K)
Posted by: Bob from NSA at December 23, 2020 04:57 PM (w46x0)
Posted by: Joe Biden at December 23, 2020 04:57 PM (n/x6m)
It passed with veto-proof majorities so next week Trump is getting humiliated yet again when his veto gets overridden by congressional votes.
Never has a man enjoyed being humiliated as much as Trump.
Posted by: Trump loves losing at December 23, 2020 04:57 PM (bxwiJ)
Step 1. Buzzword, computer lingo, drive configuration, driver, firmware, partitio, 4096 bit, 128 character password, blah blah blah.
.....
Step infinity plus 4. More blah blah blah.
....
Step tl;dr
....
Ta da!
Posted by: Officer Gunther Toody and Officer Francis Muldoon at December 23, 2020 04:58 PM (l3SuK)
no cheap pseudo-random for us, get the best !
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 04:58 PM (pmEbq)
POP also used to send your password in the clear, like FTP and a whole bunch of tools that came from a time where people were primarily concerned with making things work instead of worrying about motivated attackers.
Posted by: Ace's liver at December 23, 2020 04:58 PM (wGeit)
Posted by: SMOD at December 23, 2020 04:57 PM (3aI0K)
I want a skull-gun.
Posted by: hogmartin at December 23, 2020 04:58 PM (t+qrx)
Posted by: Notsothoreau - look forward at December 23, 2020 04:58 PM (YynYJ)
Posted by: Bob from NSA
Makes sense. Feds have been backdooring the whole country since at least 1913.
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 04:58 PM (SchxB)
The point of encryption is not that you have something to hide. The point is that your business is nobody's business, including big tech, big brother, or big government.
Anyone with two brain cells to kill with alcohol that has lived through the past four years should instantly recognize the value of keeping your affairs and effects private.
Also, second on Thunderbird and Enigmail addon.
Posted by: PhlounDer, Ayatollah-Elect of Rock-n-Rolla at December 23, 2020 04:59 PM (KnJdm)
Posted by: free tibet at December 23, 2020 04:59 PM (UavM2)
Posted by: Hillary at December 23, 2020 04:59 PM (OFJlJ)
Vote harder.
Posted by: deplorable unperson - r
what is the stock ticker?
Posted by: confederatefifth at December 23, 2020 05:00 PM (4Jold)
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 04:58 PM (pmEbq)
I knew a guy who used avalanche diode breakdown noise to seed a RNG.
Posted by: hogmartin at December 23, 2020 05:01 PM (t+qrx)
Posted by: SFGoth at December 23, 2020 05:02 PM (KAi1n)
Posted by: Jewells45TRUMPWON! at December 23, 2020 05:02 PM (nxdel)
Posted by: Notsothoreau - look forward at December 23, 2020 05:02 PM (YynYJ)
* looks at "Not secure" next to the URI in my browser *
Next time, document the process for enabling TLS on websites while leveraging a free "Let'sEncrypt!" certificate.
Posted by: antisocial justice beatnik at December 23, 2020 05:03 PM (DTX3h)
Posted by: Jeffrey Toober at December 23, 2020 05:03 PM (WQZ1O)
They "modernized" by off loading the entire agency's email to Google. They put a nice government sticker on the web client, but geeze, giving Google all your shit like that was stupid then just as it's stupid now.
Posted by: Martini Farmer at December 23, 2020 05:03 PM (3H9h1)
Posted by: Notsothoreau - look forward at December 23, 2020 04:58 PM (YynYJ)
Thank you for offering. It really is a lot easier to explain one-on-one, or at least somewhere with coffee and a dry-erase board, and bagels.
Posted by: hogmartin at December 23, 2020 05:03 PM (t+qrx)
@GaSecofState made backroom deal with Dems to change absentee ballots
without approval of legislature." Bought? As in, with his own money??
Posted by: davidt at December 23, 2020 05:03 PM (l3+k2)
Can't I simply use my Little Orphan Annie decoder ring for secure communications?
Posted by: Tonypete at December 23, 2020 05:04 PM (Rvt88)
Posted by: Hills at December 23, 2020 05:04 PM (2cfUo)
Posted by: Notsothoreau - look forward at December 23, 2020 05:04 PM (YynYJ)
Had a lot of backing, right up until every potential investor would be visited by men in black suits from the US Government.
It was explained that DarkMail HAD to have nefarious interests, and they would use supporting it as probable cause to look at everything supporters had ever done.
Needless to say, project died.
Posted by: Romeo13 at December 23, 2020 05:04 PM (oHd/0)
Posted by: hogmartin
Well, good bagels.
Posted by: Tonypete at December 23, 2020 05:04 PM (Rvt88)
Posted by: alexthechick - Boobs and hysteria at December 23, 2020 04:51 PM (GbPPJ)
The counter to that is opposing counsel discovery - don't talk about your competitor or the defendant you are suing to other idiots in the company that negates what you found in their emails...and let me tell you, having been in dozens of these now, this is always...fucking always is the case....the judge will not be amused.
You see, a law suit, seemingly unbeknownst to many - is a two way street. Often the plaintiff loses. A lot.
Posted by: Boswell at December 23, 2020 05:04 PM (w2LAm)
C'mon my balls can be quite endearing once you get used to them.
Posted by: Dr. Bone at December 23, 2020 05:05 PM (WOYcU)
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 04:58 PM (pmEbq)
I knew a guy who used avalanche diode breakdown noise to seed a RNG.
Posted by: hogmartin at December 23, 2020 05:01 PM (t+qrx)
You can buy true random noise generators as a card for your PC. They're almost all based on some quantum mechanics trick.
Posted by: Ace's liver at December 23, 2020 05:05 PM (wGeit)
https://tinyurl.com/ybn4ktmb
Posted by: Jewells45TRUMPWON! at December 23, 2020 05:02 PM (nxdel)
You'd think I'd have learned by now.
And just how is saggy moobs considered buff? Fooker is weak and pillowy.
and Mike is just terrifying.
Posted by: Pug Mahon, Confuzzled at December 23, 2020 05:05 PM (x8Wzq)
Miracle: Government Feeds Five People With Just 2.3 Trillion Loaves And Fishes
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 05:06 PM (+y/Ru)
Posted by: garrett at December 23, 2020 05:06 PM (R7m+r)
I did Medical IT work at the end of my career.
Retired when suddenly every Doctors mail and most records were suddenly 'on the cloud'.
Which breaks HIPAA all to hell, but no one seemed to care.
Posted by: Romeo13 at December 23, 2020 05:07 PM (oHd/0)
Vote harder.
Posted by: deplorable unperson - r
...
what is the stock ticker?
Posted by: confederatefifth at December 23, 2020 05:00 PM (4Jold)
Well... I only found this, and Bloomberg includes both public and private companies:
https://www.bloomberg.com/ profile/company/3614901Z:CN
(gotta love the classifications - industrial? right... asshoes)
Posted by: Helena Handbasket at December 23, 2020 05:07 PM (02b6n)
I thought the same. He's got moobs. Mooch looks so bad I don't even have words. This is the couple everyone supposedly adores?
Posted by: Jewells45TRUMPWON! at December 23, 2020 05:08 PM (nxdel)
Posted by: Notsothoreau - look forward at December 23, 2020 05:04 PM (YynYJ)
I figure you know, but it's worth pointing out, in case anyone wasn't sure - a VPN and encrypted email are two different things. You can have a VPN service on every device and still have your email completely unsecured. One is not the other.
Posted by: hogmartin at December 23, 2020 05:09 PM (t+qrx)
Loeffler owns entire stock exchanges and is worth 800 million dollars.
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 05:10 PM (3P/5p)
Posted by: hogmartin at December 23, 2020 05:11 PM (t+qrx)
https://tinyurl.com/ybn4ktmb
Posted by: Jewells45TRUMPWON! at December 23, 2020 05:02 PM (nxdel)
This is the kind of fawning you see by government controlled press in authoritarian countries.
That's not a coincidence.
Posted by: Ace's liver at December 23, 2020 05:11 PM (wGeit)
https://www.bloomberg.com/ profile/company/3614901Z:CN
(gotta love the classifications - industrial? right... asshoes)
Posted by: H
yeah, it is a private company so, nobody was buying stock outside of a special trans. in it, ever.
this is what is known as disinformatin and or idiocy.
Posted by: confederatefifth at December 23, 2020 05:13 PM (4Jold)
Loeffler owns entire stock exchanges and is worth 800 million dollars.
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 05:10 PM (3P/5p)
Well how nice for her.... *spit*
Posted by: Helena Handbasket at December 23, 2020 05:13 PM (02b6n)
Loeffler owns entire stock exchanges and is worth 800 million dollars.
Posted by: d
no she is not, quit bsing
Posted by: confederatefifth at December 23, 2020 05:14 PM (4Jold)
https://tinyurl.com/ybn4ktmb
Posted by: Jewells45TRUMPWON! at December 23, 2020 05:02 PM (nxdel)
Big Mike has really packed on some pounds and if it's possible he's gotten uglier.
Posted by: TheQuietMan at December 23, 2020 05:14 PM (UnQ9z)
Posted by: confederatefifth at December 23, 2020 05:15 PM (4Jold)
https://tinyurl.com/ybn4ktmb
Posted by: Jewells45TRUMPWON!
Well, just makes sense to bring a sasquatch on a kayack trip.
Posted by: Anonosaurus Wrecks, Tyrannosaur Wrangler at December 23, 2020 05:15 PM (+y/Ru)
Bwahaha..... it's so true.
Posted by: redridinghood at December 23, 2020 05:15 PM (NpAcC)
Posted by: Braenyard at December 23, 2020 05:16 PM (CZm2G)
Posted by: Mr Aspirin Factory at December 23, 2020 05:16 PM (89T5c)
Loeffler owns entire stock exchanges and is worth 800 million dollars.
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 05:10 PM (3P/5p)
A lot of politicians are bored spouses of wealthy business men/women - and these people invest in a lot of shit. I seriously doubt, after hearing Loeffler speak, that she's an 'informed' investor as meant by the Securities Law of 1933. She's a rich dumbass that wants to be a Senator, that's about it.
Posted by: Boswell at December 23, 2020 05:18 PM (w2LAm)
Any help?
Posted by: Deplorable Jay Guevara at December 23, 2020 05:20 PM (GArKj)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 05:21 PM (SchxB)
It's written all over his face.
Posted by: Braenyard at December 23, 2020 05:21 PM (CZm2G)
Posted by: blake - Dr semi lurker in marginal standing at December 23, 2020 05:24 PM (WEBkv)
Posted by: Deplorable Jay Guevara at December 23, 2020 05:20 PM (GArKj)
Windows 10? It might be added in the accounts settings in Windows. You could try doing the install and then removing her account and adding yours after that. I'm not really a Windows guy, sorry
Posted by: hogmartin at December 23, 2020 05:24 PM (t+qrx)
Posted by: Braenyard at December 23, 2020 05:24 PM (CZm2G)
Oh yeah, the Dems are back in town
the dems are back in town
Posted by: Braenyard at December 23, 2020 05:26 PM (CZm2G)
Posted by: Blanco Basura - moronhorde.com lives again at December 23, 2020 05:27 PM (SchxB)
Posted by: Deplorable Jay Guevara at December 23, 2020 05:20 PM (GArKj)
You also might be able to cancel out of the out-of-the-box config and then do the "set up an existing address" after that. It might be just in the initial setup configurator.
Posted by: hogmartin at December 23, 2020 05:27 PM (t+qrx)
Posted by: ... at December 23, 2020 04:02 PM (LCUUO)
-----------
Ha, I checked - I'm on version 35 of 78.
Posted by: Braenyard at December 23, 2020 05:28 PM (CZm2G)
Posted by: Berserker-Dragonheads Division at December 23, 2020 04:08 PM (9Om/r)
I am using a real old version of Thunderbird; have had it for years and years. I have never used Outlook.
Posted by: Alberta Oil Peon at December 23, 2020 05:29 PM (mzC78)
Posted by: Deplorable Jay Guevara at December 23, 2020 05:31 PM (GArKj)
Posted by: Alberta Oil Peon at December 23, 2020 05:29 PM (mzC7
The enigmail plug-in should be available for older versions, too. The end-to-end encryption is built into the new versions, so it's not necessary unless you're using older versions.
Posted by: hogmartin at December 23, 2020 05:34 PM (t+qrx)
In the upper right corner of Thunderbird is a "hamburger" icon (3 horizontal lines). Click on that.
Then click on "new" and choose "Existing Email Address". From here you can setup a new account. Ignore the "Get a new email address" link in blue.
Posted by: Martini Farmer at December 23, 2020 05:36 PM (3H9h1)
(picky, picky, picky, I know)
Posted by: sock_rat_eez, we are being gaslighted 24/365 TRUMP WON! at December 23, 2020 05:37 PM (pmEbq)
Posted by: deplorable unperson - refuse to accept the Mask of the Beast at December 23, 2020 05:39 PM (3P/5p)
Posted by: Berserker-Dragonheads Division
I do everything not windows that I can.
Posted by: Braenyard at December 23, 2020 05:40 PM (CZm2G)
https://tinyurl.com/ybgdswmu
Posted by: anonymous at December 23, 2020 05:42 PM (hRoyQ)
Posted by: vmom Trump Won! at December 23, 2020 05:59 PM (nUhF0)
Posted by: hogmartin at December 23, 2020 06:06 PM (t+qrx)
Posted by: vmom Trump Won! at December 23, 2020 06:16 PM (nUhF0)
Posted by: hogmartin at December 23, 2020 06:20 PM (t+qrx)
Posted by: antisocial justice beatnik at December 23, 2020 07:06 PM (DTX3h)
not sure what version the os is - hubby's using it to play chess and I can't cgeck
recently updated I think
Posted by: vmom Trump Won! at December 23, 2020 07:32 PM (nUhF0)
Posted by: hoot at December 23, 2020 07:46 PM (CJyYh)
Posted by: CarpetheadLarRo at December 23, 2020 10:49 PM (+ITg4)
https://tinyurl.com/y7malt4r
What they do is insert a weakness into the algorithm that makes it very easy to crack if you know of it. So, decryption without keys that was supposed to take years or forever is done in almost realtime.
So, be wary.
Posted by: Arun a well wisher from India at December 24, 2020 09:02 AM (BFJ5F)
Everyone should have a basic understanding of this.
And yes- stay away from freeware encryption from China et al.
Now do Blockchain.
Posted by: Cluebat at December 24, 2020 12:13 PM (9iDV6)
Processing 0.05, elapsed 0.0727 seconds.
14 queries taking 0.0268 seconds, 354 records returned.
Page size 184 kb.
Powered by Minx 0.8 beta.
Paul Anka Haiku Contest Announcement
Integrity SAT's: Entrance Exam for Paul Anka's Band
AllahPundit's Paul Anka 45's Collection
AnkaPundit: Paul Anka Takes Over the Site for a Weekend (Continues through to Monday's postings)
George Bush Slices Don Rumsfeld Like an F*ckin' Hammer
Democratic Forays into Erotica
New Shows On Gore's DNC/MTV Network
Nicknames for Potatoes, By People Who Really Hate Potatoes
Star Wars Euphemisms for Self-Abuse
Signs You're at an Iraqi "Wedding Party"
Signs Your Clown Has Gone Bad
Signs That You, Geroge Michael, Should Probably Just Give It Up
Signs of Hip-Hop Influence on John Kerry
NYT Headlines Spinning Bush's Jobs Boom
Things People Are More Likely to Say Than "Did You Hear What Al Franken Said Yesterday?"
Signs that Paul Krugman Has Lost His Frickin' Mind
All-Time Best NBA Players, According to Senator Robert Byrd
Other Bad Things About the Jews, According to the Koran
Signs That David Letterman Just Doesn't Care Anymore
Examples of Bob Kerrey's Insufferable Racial Jackassery
Signs Andy Rooney Is Going Senile
Other Judgments Dick Clarke Made About Condi Rice Based on Her Appearance
Collective Names for Groups of People
John Kerry's Other Vietnam Super-Pets
Cool Things About the XM8 Assault Rifle
Media-Approved Facts About the Democrat Spy
Changes to Make Christianity More "Inclusive"
Secret John Kerry Senatorial Accomplishments
John Edwards Campaign Excuses
John Kerry Pick-Up Lines
Changes Liberal Senator George Michell Will Make at Disney
Torments in Dog-Hell
The Ace of Spades HQ Sex-for-Money Skankathon
A D&D Guide to the Democratic Candidates
Margaret Cho: Just Not Funny
More Margaret Cho Abuse
Margaret Cho: Still Not Funny
Iraqi Prisoner Claims He Was Raped... By Woman
Wonkette Announces "Morning Zoo" Format
John Kerry's "Plan" Causes Surrender of Moqtada al-Sadr's Militia
World Muslim Leaders Apologize for Nick Berg's Beheading
Michael Moore Goes on Lunchtime Manhattan Death-Spree
Milestone: Oliver Willis Posts 400th "Fake News Article" Referencing Britney Spears
Liberal Economists Rue a "New Decade of Greed"
Artificial Insouciance: Maureen Dowd's Word Processor Revolts Against Her Numbing Imbecility
Intelligence Officials Eye Blogs for Tips
They Done Found Us Out, Cletus: Intrepid Internet Detective Figures Out Our Master Plan
Shock: Josh Marshall Almost Mentions Sarin Discovery in Iraq
Leather-Clad Biker Freaks Terrorize Australian Town
When Clinton Was President, Torture Was Cool
What Wonkette Means When She Explains What Tina Brown Means
Wonkette's Stand-Up Act
Wankette HQ Gay-Rumors Du Jour
Here's What's Bugging Me: Goose and Slider
My Own Micah Wright Style Confession of Dishonesty
Outraged "Conservatives" React to the FMA
An On-Line Impression of Dennis Miller Having Sex with a Kodiak Bear
The Story the Rightwing Media Refuses to Report!
Our Lunch with David "Glengarry Glen Ross" Mamet
The House of Love: Paul Krugman
A Michael Moore Mystery (TM)
The Dowd-O-Matic!
Liberal Consistency and Other Myths
Kepler's Laws of Liberal Media Bias
John Kerry-- The Splunge! Candidate
"Divisive" Politics & "Attacks on Patriotism" (very long)
The Donkey ("The Raven" parody)
